Phishing is a cybercrime where attackers impersonate legitimate entities to deceive individuals into sharing sensitive information, such as passwords, account details, or financial data.
Recognizing phishing attempts is crucial for safeguarding business assets and ensuring the confidentiality of critical information.
Creating awareness and fostering a proactive approach to identifying phishing scams can significantly reduce risks.
Common Red Flags of Phishing Attempts
Phishing scams often exhibit recognizable patterns that can help individuals identify and avoid falling victim to them. These red flags serve as warning signs that the email or message may not be legitimate. Here’s an expanded look at the most common indicators:
Suspicious Email Addresses
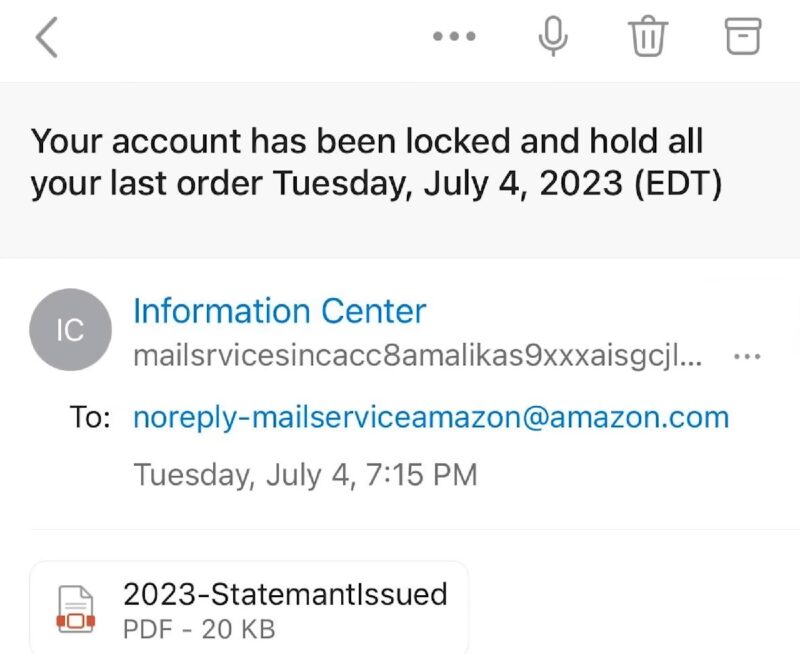
Phishing emails often come from addresses that appear genuine but include slight misspellings or extra characters. For example, instead of support@amazon.com, the email may come from support@amzon.com or support@amazon-secure.com.
This subtlety can be easy to miss, especially when someone is scanning an email quickly. Always cross-check the sender’s address carefully and compare it with the official email domain of the organization. Furthermore, you can use Zero GPT to check whether the content of an email is already used in some kind of phishing.
Generic Greetings and Sign-offs
Impersonal salutations such as “Dear Customer,” “Dear User,” or “Valued Client” are a common tactic used by scammers.
Legitimate organizations, especially those with which you have accounts, usually address you by your name. If the email doesn’t feel personalized, it’s a good reason to be cautious.
Urgent or Threatening Language
Scammers often craft emails designed to induce panic or urgency. Subject lines like “Your account will be locked in 24 hours!” or “Immediate action required to secure your account” pressure individuals to act without thinking.
This tactic plays on emotions, encouraging people to bypass critical judgment and follow the scammer’s instructions.
Unexpected Attachments or Links
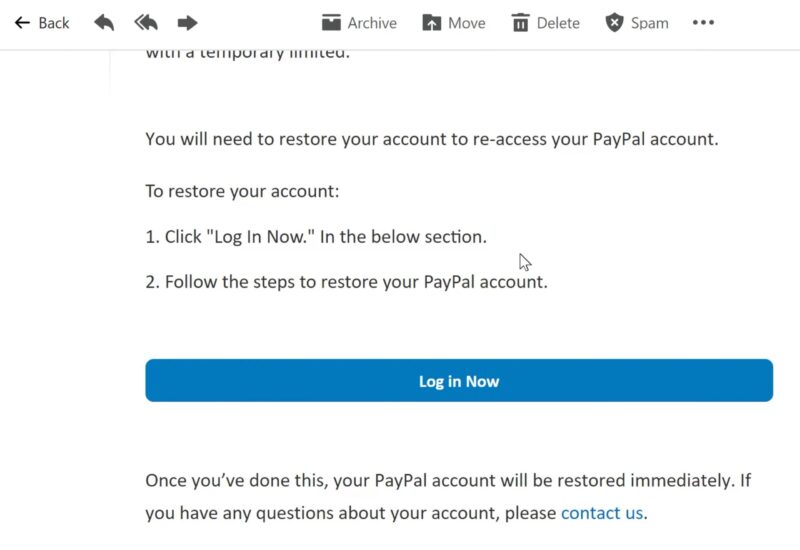
Receiving unsolicited attachments or links is one of the biggest red flags. Scammers frequently use these to deliver malicious software or direct victims to fake login pages.
Avoid clicking on links or downloading attachments unless you are absolutely certain of their legitimacy. If unsure, contact the sender through official channels to verify the message.
Requests for Sensitive Information
Most reputable companies will never ask for sensitive information, such as login credentials, social security numbers, or credit card details, via email.
If you receive a message requesting this type of information, especially under the guise of security verification, consider it suspicious.
Poor Grammar and Spelling Mistakes
Many phishing emails are riddled with spelling errors, incorrect punctuation, and awkward sentence structures. These errors often indicate that the email did not originate from a professional organization.
Legitimate companies typically maintain high communication standards, making errors a significant warning sign.
Mismatched URLs
Links within phishing emails are often disguised to appear legitimate. Hovering over a link without clicking will reveal the actual destination URL.
If the revealed link differs from what the text suggests or if it looks suspicious (e.g., includes random characters or redirects to a strange domain), do not click.
Unusual Requests
Phishing emails may include out-of-the-ordinary requests, such as transferring large sums of money, sharing confidential data, or performing other actions outside the standard processes of your organization.
These requests often target employees who might not be familiar with all protocols.
Too Good to Be True Offers
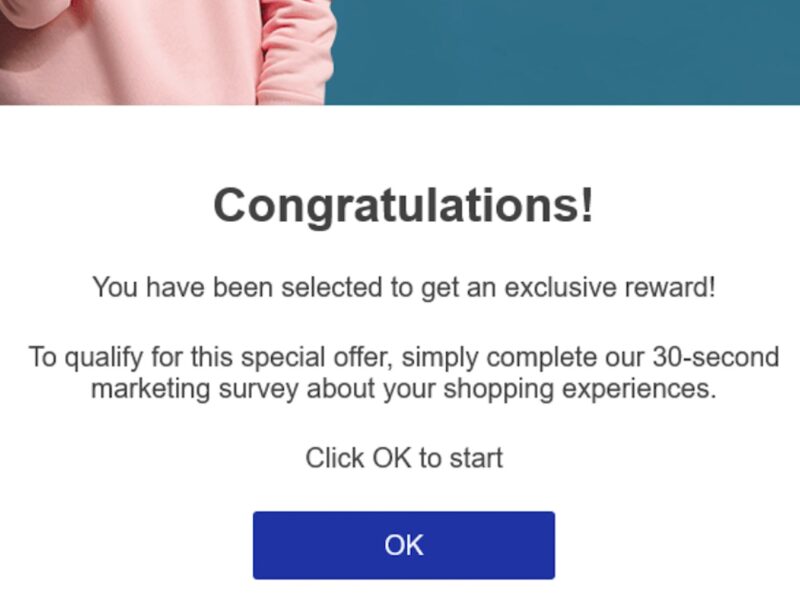
Scammers may entice recipients with promises of unrealistic rewards, such as winning a lottery you never entered, massive discounts, or expensive gifts for no reason.
As tempting as such offers might sound, they are almost always a trap designed to lure you into providing personal information.
Unfamiliar or Unexpected Sender
Emails arriving unexpectedly, particularly when you do not recognize the sender, should raise suspicion.
This is especially true if the sender claims to represent a trusted organization but does so with limited context or unfamiliar contact details. If the email feels out of place, trust your instincts and verify its authenticity.
Types of Phishing Attacks
Phishing attacks come in various forms, each meticulously designed to exploit specific vulnerabilities and achieve the attacker’s malicious goals.
Below is an expanded explanation of the most common types of attacks:
Email Phishing
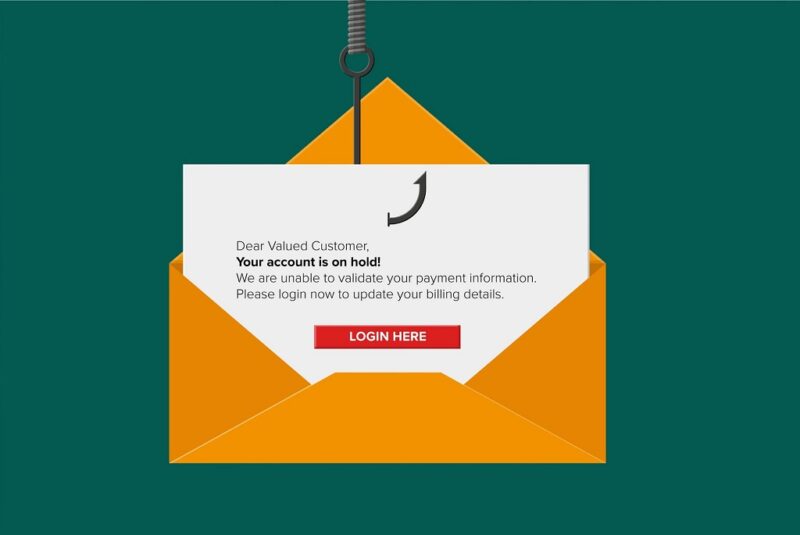
This is the most widely recognized and commonly employed phishing method. Attackers send deceptive emails that appear to originate from legitimate sources, such as banks, social media platforms, or well-known companies.
The goal is often to trick recipients into clicking on a malicious link, downloading an infected attachment, or providing sensitive information like passwords or financial details. For instance, an email might falsely claim that your account has been compromised, urging you to “verify” your credentials via a fraudulent link.
Email phishing is prevalent because it can target large groups of people simultaneously, increasing the chances of success.
Spear Phishing
Unlike email phishing, which casts a wide net, spear phishing is highly targeted. These attacks focus on specific individuals, often those in high-ranking positions or with access to sensitive data within an organization.
For example, an attacker might send an email that seems to come from a colleague or supervisor, requesting login credentials or approval for a financial transaction. The personalization makes these attacks particularly dangerous, as they are harder to detect.
Smishing and Vishing
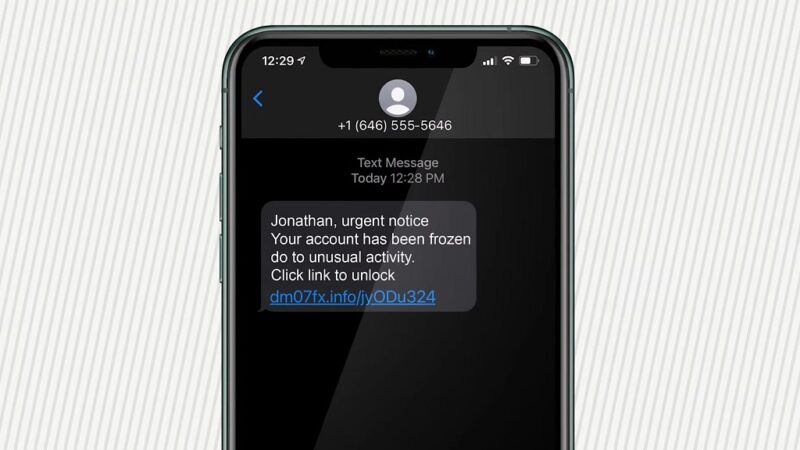
Smishing (SMS phishing) and vishing (voice phishing) are variations of phishing that exploit communication channels other than email.
In smishing, attackers send text messages containing malicious links or instructions to provide personal information. For instance, you might receive a text claiming your bank account has been locked, urging you to click on a link to resolve the issue.
Vishing, on the other hand, involves voice calls where attackers impersonate legitimate entities, such as bank representatives or government officials. The caller may use intimidation or urgency to coerce the victim into divulging sensitive information or transferring funds.
Clone Phishing
In this sophisticated attack, cybercriminals duplicate a legitimate email that the victim has previously received, such as a transactional email or a communication with an attachment.
The attacker modifies the email by replacing links or attachments with malicious ones while keeping the original content intact.
Because the email appears identical to a genuine one, recipients are more likely to trust it and interact with its malicious components.
Clone phishing is often used to target individuals who are already familiar with the sender or the content of the original email.
Recent Trends in Phishing Scams
Cybercriminals continuously adapt and evolve their tactics, creating more sophisticated and harder-to-detect scams.
These modern approaches leverage technology and human psychology in new ways, making it imperative for individuals and businesses to remain informed about these trends.
Below is an expanded look at some of the latest developments in scams:
Use of QR Codes
Scammers are increasingly embedding malicious links into QR codes, taking advantage of their growing popularity for contactless payments, restaurant menus, and promotional campaigns.
Unlike traditional links, QR codes obscure the URL destination, making it challenging for users to verify where they lead before scanning.
For example, a scammer might place fake QR codes in high-traffic areas, such as parking lots or public spaces, claiming they link to payment portals or special offers.
Once scanned, these codes can redirect users to malicious websites designed to steal personal information or install malware.
Exploiting Current Events
Attackers are adept at using current news, crises, or global events as themes for their phishing campaigns.
These scams often capitalize on heightened emotions and urgency. For instance, during natural disasters, phishing emails may masquerade as requests for donations to aid relief efforts.
Similarly, during global health crises, scammers might send emails posing as government agencies or health organizations, urging recipients to click on links for “important updates” or vaccine appointments.
The relevance of these themes increases the likelihood of victims engaging with fraudulent messages.
Advanced Spoofing Techniques
Phishers are creating highly sophisticated replicas of legitimate websites and emails, complete with accurate branding, logos, and professional design elements.
These replicas are often nearly indistinguishable from the genuine article, tricking even cautious users into entering sensitive information. For example, a spoofed login page for a popular service like PayPal or Google might perfectly mimic the original, except for a minor difference in the URL that can easily go unnoticed.
These advanced techniques highlight the importance of verifying websites and emails carefully.
Deepfake Audio and Video
An emerging trend involves the use of deepfake technology to impersonate individuals through audio or video.
For instance, attackers can create convincing voice recordings or video messages of company executives, instructing employees to complete tasks such as transferring funds or sharing confidential data.
The form of phishing is particularly dangerous in corporate settings, where employees may feel compelled to comply with instructions appearing to come from higher-ups.
The Bottom Line
Vigilance and awareness remain the strongest defenses against phishing.
Encouraging a security-conscious culture within businesses ensures that every team member plays a role in protecting sensitive information.
By staying informed and proactive, companies can reduce the risks posed by these ever-evolving cyber threats.

